ازالة فيروس Virus/.Litar و استعادة الملفات Remove Ransomware (Recover Files)
(Restore, Decrypt .litar files)
هام : هناك فرق بين remove و Decrypt
الفيروس بيشفر الملفات على الكمبيوتر ثم بيقوم بحذف النسخة الاصلية و يترك المشفرة
وفى هذه الحالة يجب عمل فك تشفير باحد البرامج اما عمل remove فده مش هيعالج التشفير
ده هيشيل الفيروس فقط من ملفات النظام حتى لا يتكرر مع ملفات اخرى.
Litar file virus infection. It is a new variant of malicious software that infects a system, restricts user access to documents, photos and music, by encrypting them, until a ransom is paid to unlock (decrypt) them. This article will provide you with all the things you need to know about ransomware virus, how to remove Litar file virus from your computer and how to restore (decrypt) encrypted photos, documents and music for free.
Litar ransomware virus is a new generation of crypto virus that encrypts photos, documents and music on harddisks and attached network disks, then requires crypto currency (Bitcoins) for payment to decrypt them . It is known to encrypt almost all file types, including files with extensions:
How to decrypt .litar files.kdc, .wpl, .zif, .cer, .psk, .wsd, .rgss3a, .rtf, .zabw, .ods, .ai, .wri, .zip, .hkx, .rim, .d3dbsp, .xf, .mdb, .xdl, .x3f, .bar, .wmf, .mddata, .vdf, .zip, .yal, .cdr, .cas, .ntl, .desc, .xwp, .lrf, .mdf, .lvl, .sid, .rofl, .wp7, .odb, .erf, .wn, .docx, .m2, .xlsx, .pdd, .wma, .3ds, .zdb, .wsc, .ppt, .arw, .ltx, .wotreplay, .fpk, .fos, .wps, .xls, .bkp, .vpk, .apk, .map, .dazip, .w3x, .mdbackup, .rwl, .cr2, .png, .rw2, .xls, .2bp, .hvpl, .xld, .raw, .ptx, .wpa, .ibank, .wmv, .syncdb, .wpe, .t13, .hplg, .txt, .pfx, .wsh, .pptm, .das, .xll, .wav, .crt, .menu, .accdb, .snx, .odc, .1st, .iwi, .wpw, .p12, .itl, .7z, .cfr, .mp4, .pak, .webp, .p7b, .ztmp, .wbc, .asset, .ysp, .vcf, .odm, .wcf, .csv, .wpb, .bkf, .3fr, .hkdb, .0, .rar, .icxs, .wp5, .bay, .fsh, .mlx, .xlsm, .pdf, .doc, .mpqge, .ff, .nrw, .dwg, .wp4, .wma, .esm, .xmind, .epk, .bik, .sr2, .x, .z3d, .bsa, .zw, .wmo, .db0, .wmd, .wm, .wpd, .flv, .wbd, .avi, .kdb, .ws, .ybk, .y, .xlsb, .kf, .css, .litemod, .wp6, .der, .wbz, .vtf, .t12, .gdb, .pst, .re4, .vfs0, .qdf, .m4a, .wpd, .xy3, .mrwref, .iwd, .sie, .dcr, .r3d, .wbm, .m3u, .wbk, .svg, .mef, .wbmp, .srw, .jpe, .sidd, .sql, .ncf, .dba, .odt, .forge, .xlsx, .xdb, .pef, .xbdoc, .p7c, .bc6, .wp, .xpm, .sum, .blob, .xml, .rb, .wdb, .bc7, .wps, .sis, .psd, .itm
The encryption algorithm is so strong that it is practically impossible to decrypt .litar files without the actual encryption key. Should you pay the ransom? A majority of cyber security specialists will reply immediately that you should never pay a ransom if affected by ransomware! If you choose to pay the ransom, there is no 100% guarantee that you can decrypt all files!
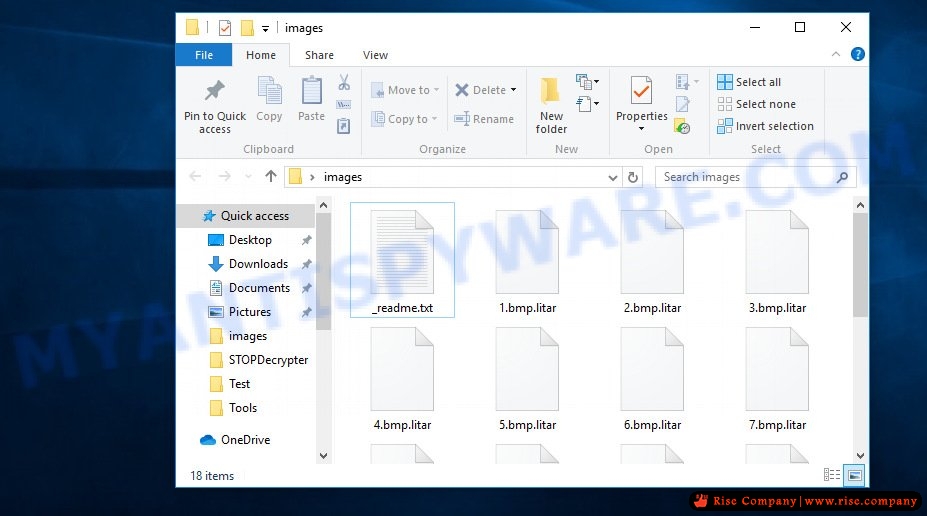
Files encrypted by .Litar ransomware virus
With some variants of Litar file virus, it is possible to decrypt encrypted files using free tools.
Michael Gillespie (@) released the Litar decryption tool named STOPDecrypter. It can decrypt files if they were encrypted by one of the known OFFLINE KEY’s retrieved by Michael Gillespie. Please check the twitter post for more info.
https://twitter.com/demonslay335/sta...15185779957761
Litar decryption tool
STOPDecrypter is a program that can be used for Litar files decryption. One of the biggest advantages of using STOPDecrypter is that is free and easy to use. Also, it constantly keeps updating its ‘OFFLINE KEYs’ DB. Let’s see how to install STOPDecrypter and decrypt .Litar files using this free tool.
برنامج STOPDecrypter
.
download.bleepingcomputer.com/demonslay335/STOPDecrypter.zip
Installing the STOPDecrypter is simple. First you will need to
download STOPDecrypter on your Windows Desktop from the following link
- After the downloading process is done, close all applications and windows on your machine. Open a file location. Right-click on the icon that’s named STOPDecrypter.zip.
- Further, select ‘Extract all’ and follow the prompts.
- Once the extraction process is finished, run STOPDecrypter. Select Directory and press Decrypt button.
If STOPDecrypter does not help you to decrypt encrypted files, in some cases, you have a chance to recover your files, which were encrypted by the Litar file virus. This is possible due to the use of the tools named ShadowExplorer and PhotoRec. An example of recovering encrypted files is given below.
على من يريد فك تشفير الملفات قراءة ملف الفدية txt
بداخله ال id ويرى هل لديك الـ id الخاص بك (تجده في رسالة الرانسوموير)
الأداة فقط تفك هذا الأي دي حاليا
A few notes. This decrypter currently only works for personal ID 6se9RaIxXF9m70zWmx7nL3bVRp691w4SNY8UCir0 (the offline key used if the malware failed to get a key from its server), or if you have the key.كود:6se9RaIxXF9m70zWmx7nL3bVRp691w4SNY8UCir0
اذا فشل الرانسوموير في الإتصال بالإنترنت فانه يستخدم هذا الأي دي لتشفير الملفات
لمعرفة الأي دي دي سوف يكون موجود في اول 43 حرف من ااي ملف مشفر او في رسالة الرانسوموير
+ إنشاء موضوع جديد
النتائج 1 إلى 1 من 1
-
16-07-2019, 12:25 #1Status
- Offline





- تاريخ التسجيل
- Apr 2014
- الدولة
- Egypt
- المشاركات
- 4,619
 Engineering and Technology
Engineering and Technology
- معدل تقييم المستوى
- 10
 فيروس الفدية Ransomware فيروس ليتر Litar virus ازالة وفك التشفير Decrypt
------------------------------------------------------------------------
فيروس الفدية Ransomware فيروس ليتر Litar virus ازالة وفك التشفير Decrypt
------------------------------------------------------------------------
شركة رايز للهندسة و التكنولوجيا Rise Company for Engineering & Technology
------------------------------------------------------------------------
Web Hosting | Web Designing | E-Marketing
رقم # 1 فى خدمات الشركات Business Services
استضافة مواقع Web Hosting - عمل ايميل شركة Business Emails
تصميم موقع شركة Web Design - تسويق الكترونى على جوجل Google Adwords
www.rise.company | www.rise.company/emails
ملحوظة : جميع خدماتنا مخصصة للشركات فقط وغير متاحة للافراد
وليس لنا اى منتجات او صيانة نهائيا! يرجى الانتباه الى ذلك.
المواضيع المتشابهه
-
فيروس الفدية Ransomware فيروس جيرو gero virus ازالة وفك التشفير Decrypt
بواسطة Rise Company في المنتدى قسم الانتى فيروس Virusesمشاركات: 0آخر مشاركة: 28-08-2019, 04:18 -
تحميل فيروس إيكار EICAR Virus test file لاختبار استجابة مضاد الفيروسات
بواسطة Rise Company في المنتدى قسم الانتى فيروس Virusesمشاركات: 0آخر مشاركة: 23-07-2019, 16:08 -
ويندوز سيرفر Window Server الحماية من فيروس الفدية
بواسطة Rise Company في المنتدى قسم الويندوز سيرفر Windows Serverمشاركات: 0آخر مشاركة: 04-07-2019, 01:43 -
ازالة فيروس الفدية Ransomware - تريد فك التشفير Wanna Decrypt
بواسطة Rise Company في المنتدى قسم الانتى فيروس Virusesمشاركات: 0آخر مشاركة: 15-05-2017, 05:27 -
فيروس الفدية Ransomware فيروس وانا كراى WCRY Virus تقرير و وقاية شاملة
بواسطة Rise Company في المنتدى قسم الانتى فيروس Virusesمشاركات: 0آخر مشاركة: 14-05-2017, 15:34




 رد مع اقتباس
رد مع اقتباس
المفضلات