فايروول CSF Firewall حل مشكلة cpanel Suspicious File Alert /dev/shm/set
csf Reason: Linux Binary - warning: Suspicious file types found in /dev
cpanel Suspicious File Alert /dev/shm/set - webshell - /dev/shm and /tmp
cpanel Suspicious File Alert File: /dev/shm/set
disable_functions = show_source, system, shell_exec, passthru, exec, phpinfo, popen
Suspicious File Alert: Tracking where the file has come from
------------------------------------------
المشكلة:
------------------------------------------
هيصل لك ايميل على سيرفرك AlmaLinux ان هناك user على السيرفر رفع ملف تجسس
يقوم هذا الفيروس يسحب ملف config الخاص بالووردبريس لقواعد بيانات
لعملاء اخرين على نفس السيرفر وهتجد بالفعل قواعد البيانات التى سحبت
موجودة فى فولدر داخل حساب العميل بسبب فيروس مرفوع.
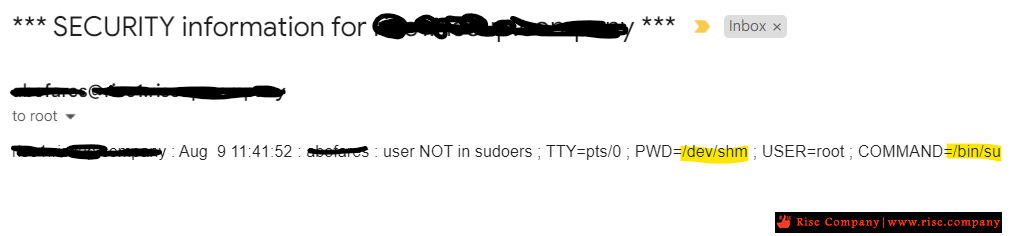
تجد هنا فى الصور ان هناك ملف file باسم set تم رفعه على dev/shm
بداخله اوامر شل نفذت هذا الامر ! والفايروول تلقائيا عمل Action
وقف هذا الملف عن العمل بنقله الى var/lib/csf/suspicious.tar
وبالفعل هتجده هناك.
وهنا يظهر ان الفايروول انتبه لذلك ووجد ان العميل user ليس sudo ويقوم بعمل root
------------------------------------------
حل المشكلة :
------------------------------------------
1- اذا كان لديك csf فايروول لا تقلق فهو بالفعل وقف هذا العمل وكذلك
اذا كنت مانع الاتصال مع قواعد البيانات من خارج السيرفر فانت فى امان
من اى اتصال خارجى مع قواعد البيانات المسربة ويفضل تغيير باسورد قواعد البيانات هذه.
2- اسخدم ImunifyAV لفحص حساب العميل واحذف حساب العميل تماما اذا كان باستطاعتك
قد يكون هناك backdoor ولا تشعر به ! يجب التحقق من الحماية لمنع حدوث مثل ذلك
فى الكلاود لينكس Cloudlinux انت محمى لان كل عمل فى قفص Cage
اما اللينكس فيجب وضع المزيد من الحماية.
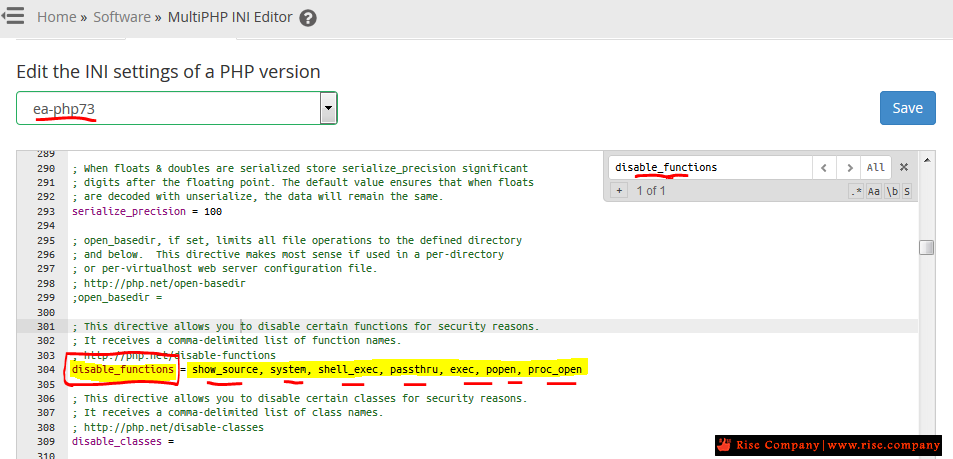
3- غلق allow_url_fopen من MultiPHP INI Editor
The allow_url_fopen is a setting managed through the PHP Options which allows PHP file functions to retrieve data from remote locations over FTP or HTTP. This option is a significant security risk, thus, do not turn it on without necessity.
The Allow_url_fopen function can retrieve information from a remote server. This function will be in deactivation server-wide for all domains on the majority of shared servers. We have to disable this since it poses a severe security risk. For security reasons, in a shared hosting account allow_url_fopen is disabled by default. Note that in a shared account the allow_url_fopen is by default disabled. The allow_url_fopen PHP option specifies whether or not PHP is permitted to fetch URL objects such as files. This feature is frequently disabled for security reasons, although some scripts may require it to function properly. Users who attempt to enable or disable this via the MultiPHP INI Editor in cPanel may notice that their scripts or PHP information pages are not updated. Disable allow_url_fopen on a Linux/cPanel Server There is a high probability for a website to get weak for hackers if the allow_url_fopen is in the activation stage on the server. So most hosting companies opt to disable it to ensure security. The probability and the chances of website compromisation if this directive is active globally on the server.
4- المسار /dev/shm و /tmp كلاهما writeable اى عميل يستطيع رفع ملفات عليه
ولا يوجد طريقة لعمل block لذلك الا من خلال حظر الدوال disable_functions فى php
كود:disable_functions = show_source, system, shell_exec, passthru, exec, phpinfo, popen, proc_open
قد يكون بعضها مفعل وليس جميعها , لذلك احظر جميعها وليس بعضها
Your basically disabling some stuff that makes it much easier to hack your server. Like anything if your not using it then no need to leave it for the world to take advantage of.
شاهد ايضا/dev/shm and /tmp are world writeable; any user can write files there. There is no 100% way to block these. ModSecurity and CXS can help. However the only way to not have your customers be infected with these is to make them keep their CMS software (joomla, wordpress, etc.) fully updated and with good strong administrative passwords. You can also set in /usr/local/lib/php.ini the disable_functions setting to disallow exec and other risky php functions. Mine is set something like:
حماية WHM / CPANEL من خلال غلق FUNCTIONS الخطرة DISABLE_FUNCTIONS
المرجع:
https://forums.cpanel.net/threads/we...nd-tmp.396252/
https://forums.cpanel.net/threads/di...o-popen.58180/
https://www.webhostingtalk.com/showthread.php?t=1456023
+ إنشاء موضوع جديد
النتائج 1 إلى 1 من 1
-
10-08-2023, 14:24 #1Status
- Offline





- تاريخ التسجيل
- Apr 2014
- الدولة
- Egypt
- المشاركات
- 4,642
 Engineering and Technology
Engineering and Technology
- معدل تقييم المستوى
- 10
 فايروول CSF Firewall حل مشكلة cpanel Suspicious File Alert /dev/shm/set
------------------------------------------------------------------------
فايروول CSF Firewall حل مشكلة cpanel Suspicious File Alert /dev/shm/set
------------------------------------------------------------------------
شركة رايز للهندسة و التكنولوجيا Rise Company for Engineering & Technology
------------------------------------------------------------------------
Web Hosting | Web Designing | E-Marketing
رقم # 1 فى خدمات الشركات Business Services
استضافة مواقع Web Hosting - عمل ايميل شركة Business Emails
تصميم موقع شركة Web Design - تسويق الكترونى على جوجل Google Adwords
www.rise.company | www.rise.company/emails
ملحوظة : جميع خدماتنا مخصصة للشركات فقط وغير متاحة للافراد
وليس لنا اى منتجات او صيانة نهائيا! يرجى الانتباه الى ذلك.
المواضيع المتشابهه
-
فايروول CSF Firewall حل مشكلة The server appears to have no swap file
بواسطة Rise Company في المنتدى قسم فايروول CSFمشاركات: 0آخر مشاركة: 08-03-2023, 21:02 -
فايروول CSF Firewall حل مشكلة RELAY Alert / RELAY, Remote IP
بواسطة Rise Company في المنتدى قسم فايروول CSFمشاركات: 0آخر مشاركة: 11-10-2022, 14:21 -
فايروول السي بانل Whm / Cpanel CSF Firewall حل مشكلة do not delete لا تعمل
بواسطة Rise Company في المنتدى قسم فايروول CSFمشاركات: 0آخر مشاركة: 05-04-2020, 17:04 -
فايروول السي بانل Whm / Cpanel CSF Firewall حل مشكلة Status: Enabled but Stopped
بواسطة Rise Company في المنتدى قسم فايروول CSFمشاركات: 0آخر مشاركة: 08-12-2018, 01:08 -
فايروول السي بانل Whm / Cpanel CSF Firewall مشكلة excessive resource usage alert
بواسطة Rise Company في المنتدى قسم فايروول CSFمشاركات: 0آخر مشاركة: 03-12-2018, 22:23






 رد مع اقتباس
رد مع اقتباس
المفضلات