فايروول CSF Firewall حماية whm / cpanel من هجمات DDoS Attack
Config Server Security & Firewall
cPanel & WHM supports the Config Server Security (CSF) firewall,
which provides a WHM plugin with a comprehensive configuration interface.
First, you will need to follow these instructions to install the plugin.
Next, navigate to the ConfigServer Security & Firewall page in the Plugins section
of the WHM sidebar menu. Scroll down and click on Firewall Configuration.
Our goal is to turn on Connection Tracking and configure the “CT_LIMIT” value, which controls how many connections the firewall allows from an IP address. During a DDoS attack, a huge number of connections may be made from the same IP, and limiting connections can help to weed out unwanted traffic.
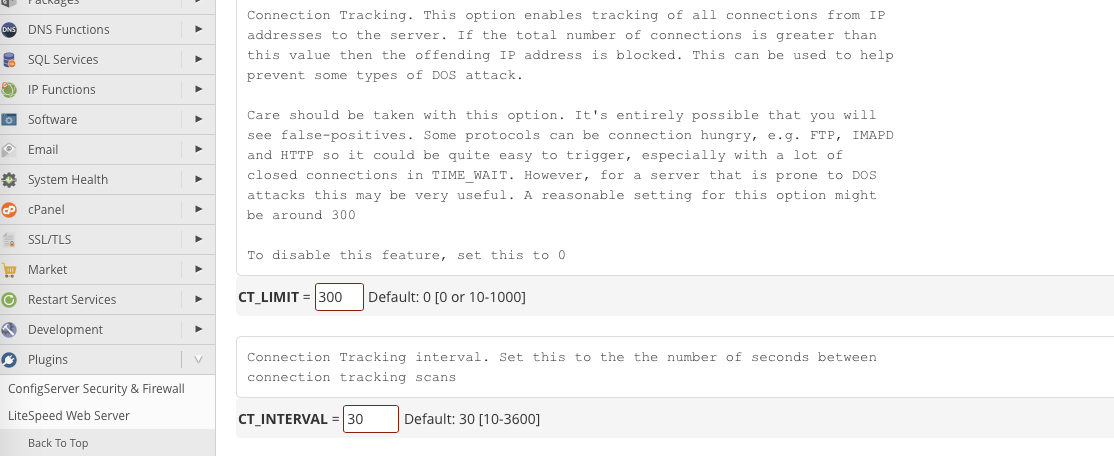
The correct value depends on the nature of the attack and typical traffic patterns, and you may want to experiment,
but 300 is a reasonable initial value. Setting this value too low may cause legitimate connections to be dropped.
You may also want to adjust the PORTFLOOD value on the same page. PORTFLOOD limits connections to a particular port.
For example, if a server experiences an attack against port 80,
the HTTP port, the following limits new connections to 50 within ten seconds, blocking subsequent attempts.
PORTFLOOD = “80;tcp;50;10”
Take a look at the CSF readme file to learn more about the PORTFLOOD syntax.
Finally, one of the most common and easy-to-implement
denial of service attacks is the Layer 4 Syn Flood. CSF includes SYN flood protection,
which you can turn on in the Port Flood Settings section of the configuration page.
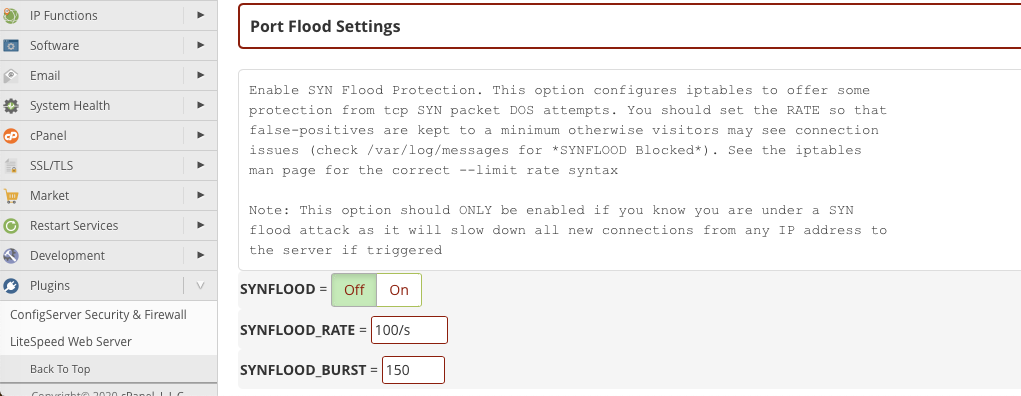
Activate SYN Flood protection and adjust the SYNFLOOD_RATE and SYNFLOOD_BURST settings.
The default may be too high to mitigate an ongoing attack. The correct values depend on the specifics of the attack,
but 75/s and 50 are a good starting point. Be aware that if you set these values too low,
legitimate traffic may face connection problems.
Syn Flood protection should only be turned on during an attack,
as it can introduce significant network latency.
المرجع:
ملحوظة هامة
Syn Flood protection should only be turned on during an attack, as it can introduce significant network latency.
It’s important to note that the presence of SYN packets does not necessarily mean that a server actually is under SYN flood attack. For instance, if load on the server already is high or there is a great deal of incoming traffic, an elevated level is to be expected. Only the presence of a large number (in the hundreds) is likely to be indicative of a possible SYN flood attack.
If you know that the server is under attack, you can configure CSF to help mitigate this type of attack.
Otherwise, skip Syn Flood and apply the rate limits you enabled up.
https://blog.cpanel.com/how-to-survive-a-ddos-attack/
https://www.liquidweb.com/kb/basic-d...-csf-firewall/
+ إنشاء موضوع جديد
النتائج 1 إلى 2 من 2
مشاهدة المواضيع
-
09-12-2021, 20:53 #1Status
- Offline





- تاريخ التسجيل
- Apr 2014
- الدولة
- Egypt
- المشاركات
- 4,628
 Engineering and Technology
Engineering and Technology
- معدل تقييم المستوى
- 10
 فايروول CSF Firewall حماية whm / cpanel من هجمات DDoS Attack
------------------------------------------------------------------------
فايروول CSF Firewall حماية whm / cpanel من هجمات DDoS Attack
------------------------------------------------------------------------
شركة رايز للهندسة و التكنولوجيا Rise Company for Engineering & Technology
------------------------------------------------------------------------
Web Hosting | Web Designing | E-Marketing
رقم # 1 فى خدمات الشركات Business Services
استضافة مواقع Web Hosting - عمل ايميل شركة Business Emails
تصميم موقع شركة Web Design - تسويق الكترونى على جوجل Google Adwords
www.rise.company | www.rise.company/emails
ملحوظة : جميع خدماتنا مخصصة للشركات فقط وغير متاحة للافراد
وليس لنا اى منتجات او صيانة نهائيا! يرجى الانتباه الى ذلك.
المواضيع المتشابهه
-
حماية whm / cpanel من هجمات DDoS Attack من خلال Apache Module: Evasive
بواسطة Rise Company في المنتدى قسم حماية Whm / Cpanelمشاركات: 1آخر مشاركة: 09-12-2021, 21:04 -
حماية الووردبريس Wordpress هجمات من نوع xmlrpc التى ترفع لود السيرفر DOS ATTACK
بواسطة Rise Company في المنتدى قسم ووردبريس WordPressمشاركات: 0آخر مشاركة: 08-04-2020, 03:02 -
هجمات DDoS Attack لاغراق موارد السيرفر من compute.hwclouds-dns.com
بواسطة Rise Company في المنتدى قسم حماية Whm / Cpanelمشاركات: 0آخر مشاركة: 01-04-2020, 02:09 -
فايروول السي بانل Whm / Cpanel CSF Firewall الحماية من ddos
بواسطة Rise Company في المنتدى قسم فايروول CSFمشاركات: 0آخر مشاركة: 04-12-2018, 15:30 -
كلاود فلير السى بانل Whm / Cpanel Cloud Flare الحماية من هجمات DDoS
بواسطة Rise Company في المنتدى قسم الكلاود فلير CloudFlareمشاركات: 0آخر مشاركة: 19-06-2018, 00:55





 رد مع اقتباس
رد مع اقتباس
المفضلات